Configure Public Key Authentication for SFTP using 1Password SSH Agent
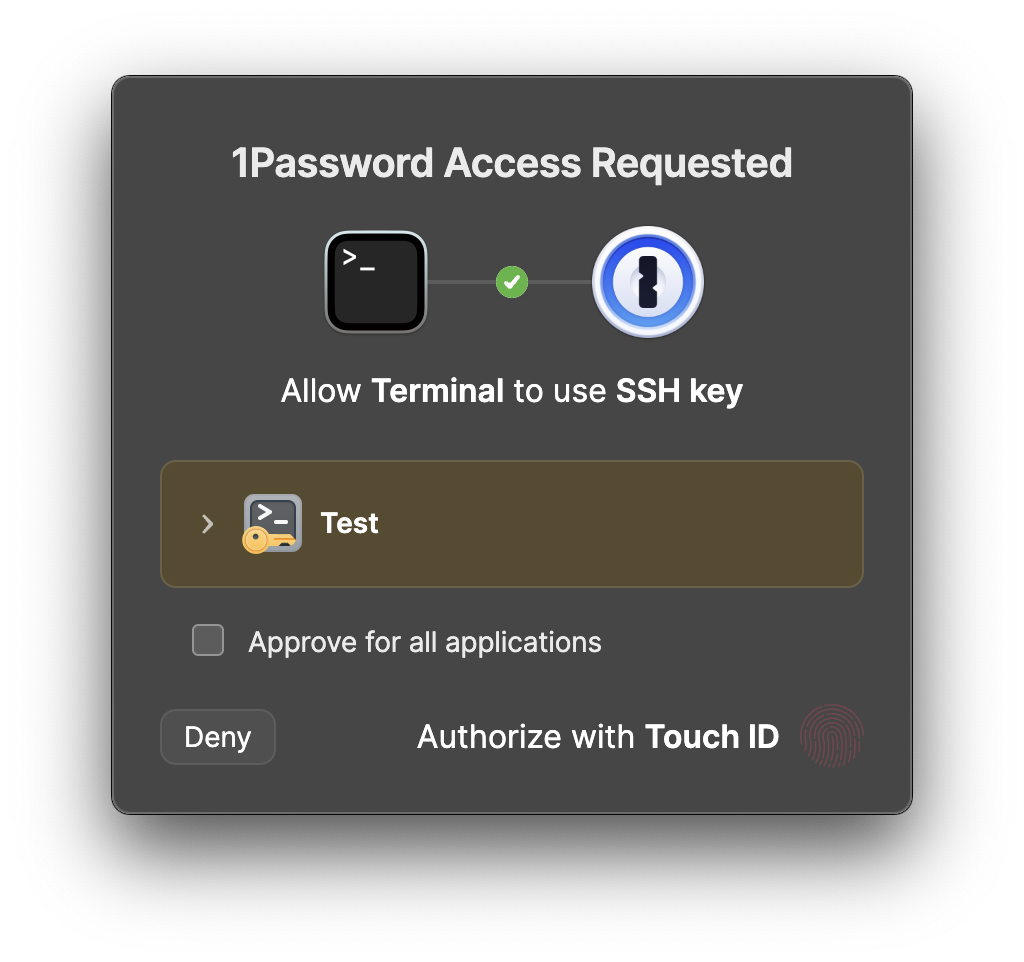
Public-key authentication using 1Password SSH Agent allows you to connect to a remote server without a password. Instead of passwords, you use a pair of keys (private and public) for authentication. The private key is kept secret, while the public key is shared with the server.
Ensure you have configured 1Password to manage your SSH keys. For more information, refer to 1Password SSH Agent. Enable the 1Password SSH Agent in 1Password → Settings… → Developer
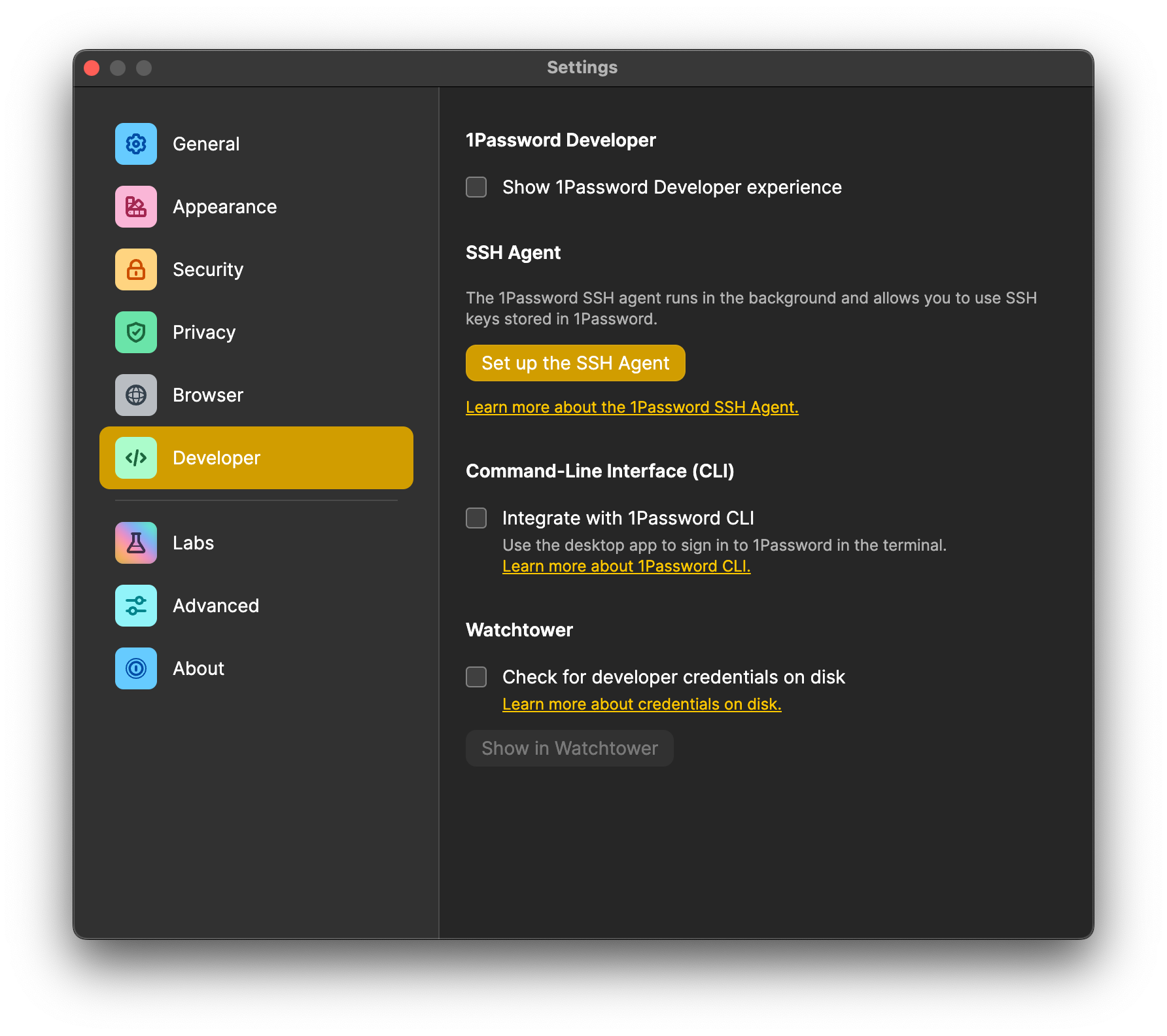
Verify the 1Password SSH Agent is running as expected by attempting to list available SSH keys with
SSH_AUTH_SOCK=~/Library/Group\ Containers/2BUA8C4S2C.com.1password/t/agent.sock ssh-add -l
Open the OpenSSH configuration file
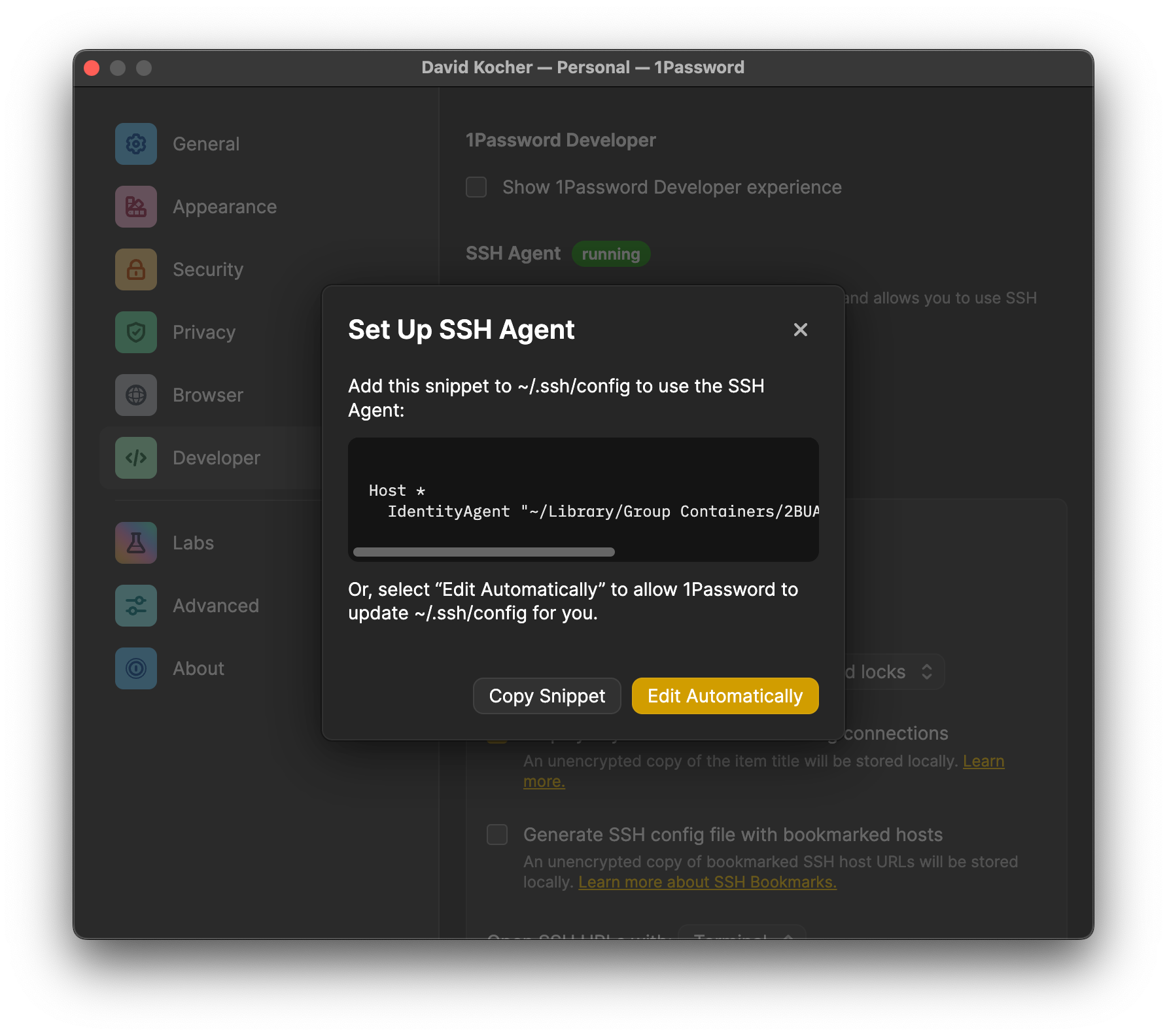
~/.ssh/configand add the following configuration specifying to use 1Password as the SSH agent:Host * IdentitiesOnly yes # 1Password SSH agent IdentityAgent "~/Library/Group Containers/2BUA8C4S2C.com.1password/t/agent.sock"
Alternatively allow 1Password to add the setting automatically:
This configuration directive is supported by Cyberduck and Mountain Duck. You can restrict the settings to a single alias in the configuration file instead of matching it for all connections with
*.Create a new SSH key in 1Password and copy the Public key to the clipboard.
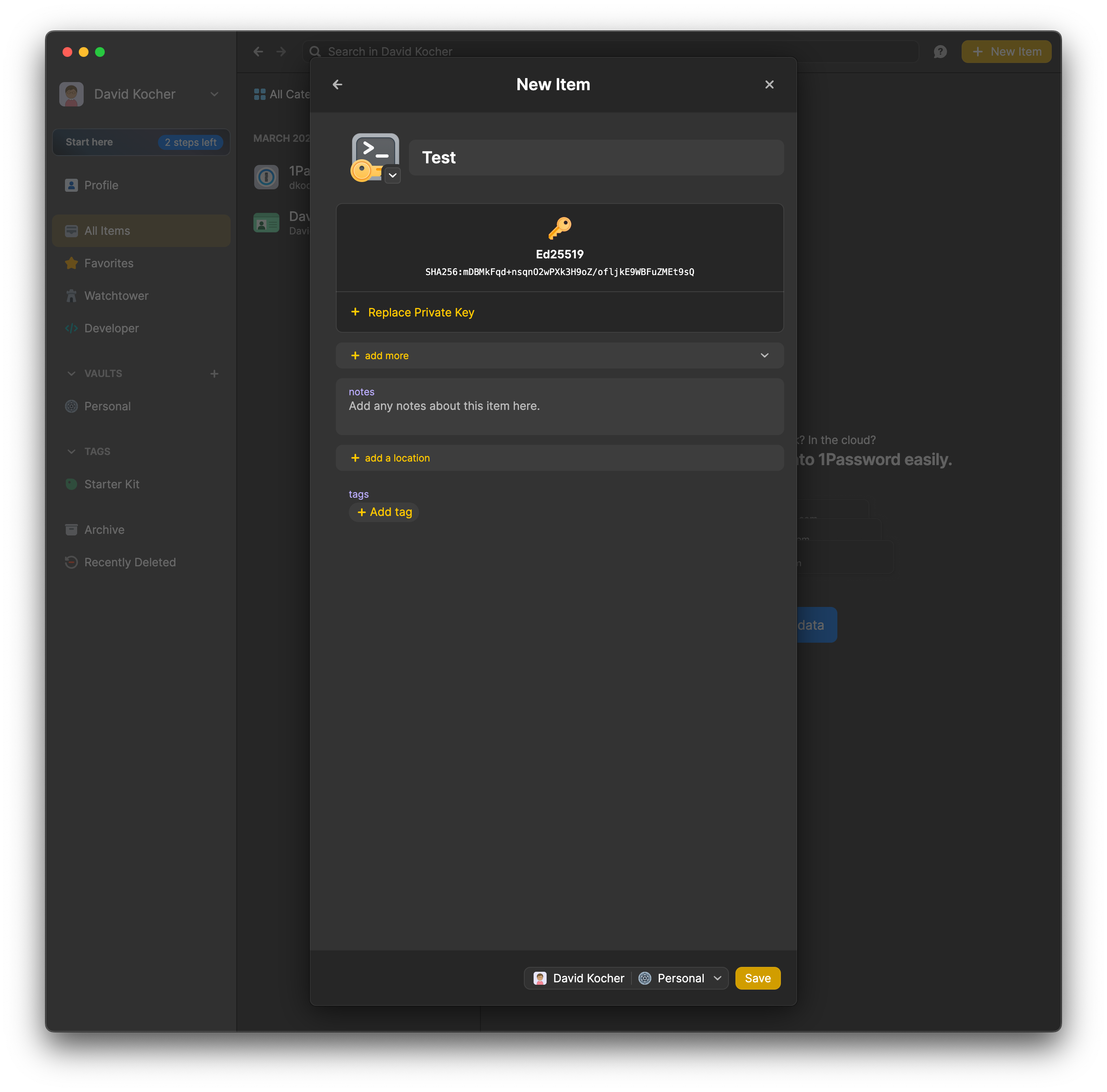
Add the public key copied from 1Password to the
authorized_keysin your~/.sshdirectory on the server running OpenSSH.pbpaste | ssh user@remotehost 'cat >> .ssh/authorized_keys
Add a new Bookmark in Cyberduck or Mountain Duck. Enter the alias from your OpenSSH configuration or the hostname in Server. You do not need to set a value for Password.
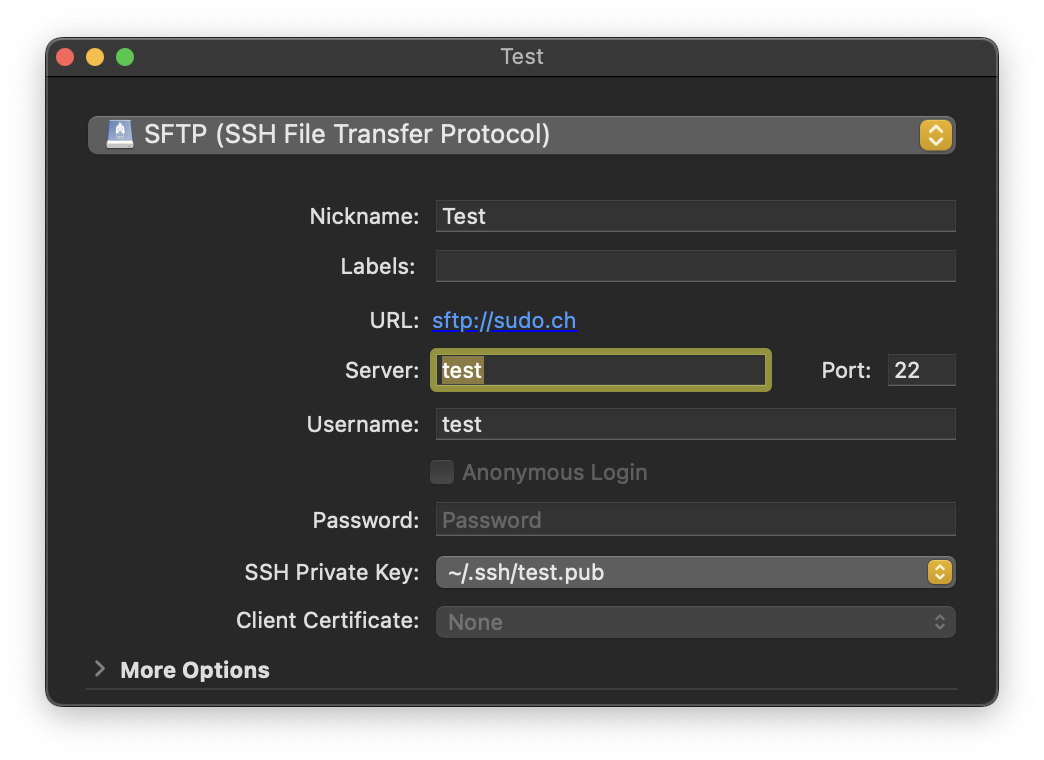
Tip
The server may respond with Too many authentication failures when trying to authenticate with all keys stored in 1Password. In the Bookmark panel, select the public key corresponding to your SSH private key saved in 1Password for SSH Private Key. The public key must be available as a file you can write from the clipboard to a file using:
pbpaste > ~/.ssh/test.pub
Alternatively, add the public key to the OpenSSH configuration file
~/.ssh/configwith theIdentityFiledirective# Public Key File used to filter identities from SSH agent IdentityFile ~/.ssh/test.pub
Connect to the server and acknowledge the prompt to use the private key stored in 1Password.